Quantum Resistant Encryption can help cybersecurity mavens not chase the code writers
A thirty something year old man originally from India and living in the United States explained his career path to cybersecurity while speaking on a podcast. His family had moved to the U.S. when he was in his teens. Career wise, his father was an engineer, and his mother was a doctor. His parents’ expectation was for their son to choose an appropriate college major to support a similar career. The son told his father he wanted to study computer science.
His father replied without missing a beat, “If you have to add the word science to the topic it isn’t a science.” The son was surprised by this response. If you think about it, though, the father has a point.
Biology, Chemistry, and Geology are all sciences with governing principles. That is why they are sciences.
What about rocket science? Actually, it is called Physics.
Political science? Behavioral science? No set rules. Dependent upon mostly unpredictable human actions and reactions. Perhaps the only absolute rule regarding these topics is that with people there are no absolutes.
Is computer science really a science? Consider these aspects.
- The world came together to write rules called the Open Systems Interconnection (OSI) model only to have the U.S. Defense Advanced Research Project Agency (DARPA) create the Transfer Control Protocol/ Internet Protocol (or IP) model which is the basis for Web 1.0 and 2.0.
- Those who study, read, write, and interpret languages like English, Latin, and Mandarin Chinese aren’t considered scientists. Why should a Python, Java, or Fortran code expert be considered a scientist? These computer languages have rules, sort of, which can have equivalent misspellings and improperly conjugated verbs and still spit out something that might be interpretable or at least exploited by a deviant code writers.
- Prominent cybersecurity podcasters develop their principles of cybersecurity, yet the list keeps growing. While it is relatively early in the development of cyber security, are there really principles if the list doesn’t end?
- However, Geoffrey Hinton, a former Google engineer, has won the Nobel Prize in Physics, of all categories, for pioneering work in the challenges around artificial intelligence.
Meanwhile, it is fully possible the next great cybersecurity solution will obviate a principle. Web 3.0 and the alleged future of rampant blockchain cryptocurrency and artificial intelligence (AI) might rewrite the cybersecurity principles. Already, AI is revamping rapid hacking and cyber defense responses. If AI can write better code than the human, what are the scientific principles that make this predictable? Or are AI users just sayin’ stuff because it sounds cool and worldly?
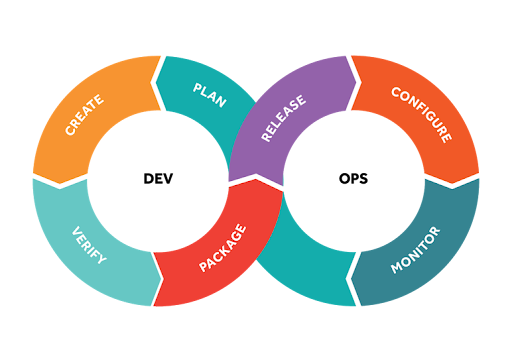
Which brings the discussion back to whether code writing is a science. Perhaps another way to consider the question is whether software engineers are even engineers. Kemper wrote, “Most software infrastructure has been largely unregulated in terms of accountability and transparency when compared to traditional infrastructure. Unlike a car, pressure vessel, or bridge, software is an ephemeral product that does not exist in a discrete physical space.” At best, software teams create code in big circles of a cycle originally called development operations, or Dev Ops (see Fig 1).
Figure 1. Dev Ops
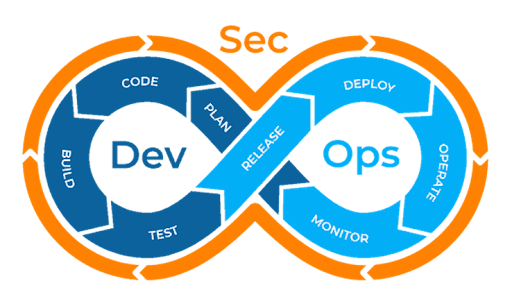
 Then, cybersecurity got involved and called it DevSecOps, See Fig 2, so security could be “baked-in” like yummy creamy melted chocolate chips in a Mrs. Fields cookie – the author and foodie is making himself hungry. Unfortunately, a recent study showed that less than four percent of all software teams include security measures during design.
Then, cybersecurity got involved and called it DevSecOps, See Fig 2, so security could be “baked-in” like yummy creamy melted chocolate chips in a Mrs. Fields cookie – the author and foodie is making himself hungry. Unfortunately, a recent study showed that less than four percent of all software teams include security measures during design.
- https://www.politico.eu/article/geoffrey-hinton-ai-artificial-intelligence-win-nobel-prize-research/
- https://www.sae.org/publications/technical-papers/content/EPR2023028/, Developing the Role of the System Software Integrator to Mitigate Digital Infrastructure Vulnerabilities
Cybersecurity mavens must be shocked to their toes by developers obviating the unofficial cybersecurity principles.
Figure 2. Dev Sec Ops
Anyway, code writing even though it involves binary ones and zeroes is as much art as it is science. Every application has infinity plus one bugs and vulnerabilities as the cybercriminals will always find one more code strand to exploit and the fixers are always fixing, and the cyber defenders are always chasing the code. Makes for a well-paying living, but the security operations center and CISO burn out rate is very high.
Maybe the best cyber security practice will be to use quantum resistant encryption which will make a lot of problems go away. Sure, it takes more computing power and thus energy. No, it won’t fix every phishing attempt, but it can make many of them more difficult to execute.
Another astute person once made the comment that scientists will solve quantum computing give or take a week of them solving containable usable nuclear fusion energy. The latter has been wishful thinking and just around the corner for humanity’s use since the Three Mile Island disaster of 1979.
Fortunately, quantum resistant encryption is already here. Many cryptologists are smacking their lips at the opportunity to debunk this haughty claim. They won’t act because they didn’t invent the noted solution, or they lack the business acumen to monetize it, or they don’t have the money to invest.
Consider this an invitation to an investor who can take ownership of the intellectual property and monetize the solution.
3. https://www.nextgov.com/cybersecurity/2024/10/few-software-developers-employ-secure-design-training-research-finds/400274/
Don’t think quantum resistant encryption is out there?
DM me. I know a guy.
- Time for a Quantum Leap - November 22, 2024
- CYBER NEEDS TO DO THE MATH - November 8, 2024
- I left my phone… A cautionary tale - December 15, 2023

